Module-OT
Module-OT protects modern power systems in which communications and controls are spread across diverse and distributed technologies. It is installed between devices and their operational technology (OT) systems to authenticate, authorize, and encrypt data at the highest standard of cybersecurity.
Functionality
Module-OT is a true plug-and-play solution for defense against vulnerabilities that exist in highly interconnected electric power systems. It is primarily designed to secure communications between distributed energy resources and control centers across wide area networks, but it can be used generally to secure utility OT networks.
The technology can be operated either as a stand-alone bump-in-the-wire device or as embedded software, and it can easily be integrated with commercial and residential distributed energy resources. Such resources include solar PV, electric vehicles, and grid-interactive buildings.
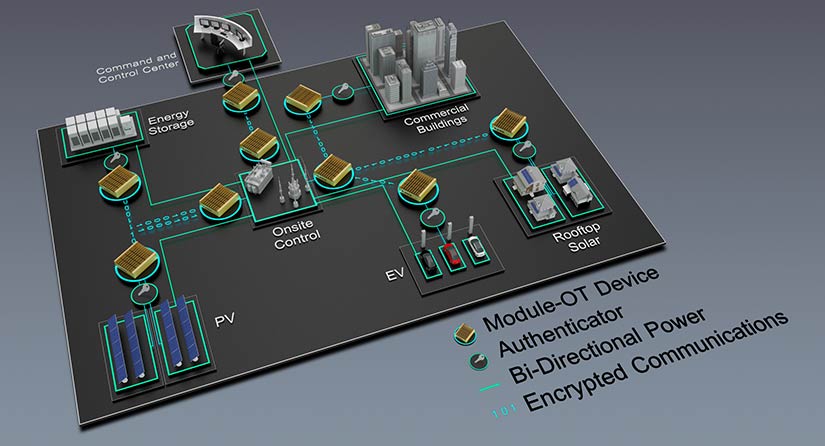
Features
Module-OT is designed to protect legacy protocols and aging devices against common cyberattacks while creating minimal obstruction to normal operations. It has low memory and processor footprints, requires minimum changes to the OT networks to operate, and ensures complete security with minimal changes to infrastructure.
Software
- Portable to a variety of architectures and Linux-based operating systems
- Easy to install, as it is readily available in popular Linux distributions such as Ubuntu and Debian
Hardware
- Low-cost, efficient, and flexible solution
- Agnostic to legacy protocols and with both aging and advanced devices
- Additional computing resources for faster encryption
Compliancy
- Supports Modbus, DNP3, and SEP 2.0
- Complies with standards IEEE 2030.5 and IEEE 1547-2018
- Communicates over serial, RS-485, wireless, and 1-GB ethernet
- Complies with Federal Information Processing Standard Publication 140-2, Level 1
- Received the National Institute of Standards and Technology's Cryptographic Algorithm Validation Program certification
- Uses hardened SSH policies
Cryptography
- Data confidentiality using Transport Layer Security
- Authentication using local PKI
- Authorization using white listing
- Key management with self-signed certificates
- System file encryption
Validations
- Evaluated communications and control security on 500-kW solar and battery site
- Simulated impacts of secure communications for distributed energy resources
- No latency disruptions—demonstrated in lab with commercial hardware devices
- Published laboratory test procedures
- Field-tested on utility distribution system
Publications
Modular Security Apparatus for Managing Distributed Cryptography for Command-and-Control Messages on Operational Technology Networks (Module-OT), NLR Technical Report (2022)
Module-OT: Modular Security Apparatus for Managing Distributed Cryptography for Command and Control Messages on Operational Technology Networks, U.S. Department of Energy Office of Cybersecurity, Energy Security, and Emergency Response Fact Sheet (2021)
ModuleOT: A Hardware Security Module for Operational Technology, NLR Technical Report (2020)
Analysis of System and Interoperability Impact from Securing Communications for Distributed Energy Resources, IEEE Power and Energy Conference at Illinois (2019)
Module OT PNM Field Demonstration Test Procedure, Sandia National Laboratories Technical Report (2019)
Cryptography Considerations for Distributed Energy Resource Systems, IEEE Power and Energy Conference at Illinois (2019)
Contact
Danish Saleem
Project Lead and Researcher, Secure Cyber-Energy Systems
Share
Last Updated Dec. 6, 2025
